Too Many Concurrent Mail Connections Try Again Ms Outlook
In nearly organizations there are several devices or applications that need to employ an SMTP service to ship email letters. An Substitution 2016 server can provide that service for y'all, however the configuration required on the server depends on the SMTP relay requirements of your scenario.
The steps for how to configure Exchange Server 2016 SMTP relay are:
- Determine whether your scenario is internal relay or external relay
- Determine whether devices and applications will authenticate or connect anonymously
- For authenticated relay, configure the TLS document for the client front end connector
- For anonymous relay, configure a new receive connector that is restricted to specific remote IP addresses
Determining Internal vs External Relay Scenarios
At that place are generally 2 types of SMTP relay scenarios that Exchange Server 2016 is used for:
- Internal relay – devices and applications that need to send email letters only to internal recipients in the Exchange system.
- External relay – devices and applications that need to send email messages to external recipients.
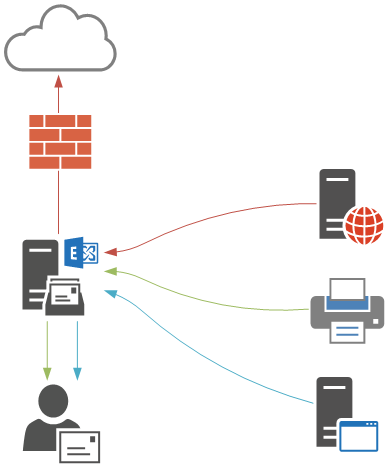
Let's take a expect at each of those scenarios, and then some additional considerations when you are deploying this in your ain production environments.
Internal SMTP Relay with Exchange Server 2016
When Exchange Server 2016 is first installed the setup routine automatically creates a receive connector that is pre-configured to be used for receiving electronic mail messages from anonymous senders to internal recipients. This allows inbound internet email to be received by the server, and is also suitable for internal relay scenarios.
The receive connector is named "SERVERNAMEDefault Frontend SERVERNAME", for example, "EXSERVERDefault Frontend EXSERVER" in my test environment.
| [ PS ] C : \ > Get - ReceiveConnector Identity Bindings Enabled -- -- -- -- -- -- -- -- -- -- -- - EXSERVER \ Default EXSERVER { 0.0.0.0 : 2525 , [ :: ] : 2525 } True EXSERVER \ Client Proxy EXSERVER { [ :: ] : 465 , 0.0.0.0 : 465 } Truthful EXSERVER \ Default Frontend EXSERVER { [ :: ] : 25 , 0.0.0.0 : 25 } True EXSERVER \ Outbound Proxy Frontend EXS . . . { [ :: ] : 717 , 0.0.0.0 : 717 } True EXSERVER \ Client Frontend EXSERVER { [ :: ] : 587 , 0.0.0.0 : 587 } True |
You lot can test this connector past making an SMTP connection using Telnet and issuing SMTP commands. For example:
| one 2 three 4 5 six 7 8 9 10 11 12 13 xiv 15 xvi 17 eighteen | C : \ > telnet exserver 25 220 EXSERVER . exchange2016demo . com Microsoft ESMTP Mail Service gear up at Thu , 22 Oct 2015 11 : 39 : 23 + 1000 helo 250 EXSERVER . exchange2016demo . com Hullo [ 192.168.0.30 ] postal service from : test @ examination . com 250 2.one.0 Sender OK rcpt to : adam . wally @ exchange2016demo . com 250 two.one.5 Recipient OK Information 354 Start mail input ; stop with . Subject : Test email Testing . 250 ii.6.0 < f7c2f921 - ff7e - 4ce4 - b2eb - a70dc52f225f @ EXSERVER . exchange2016demo . com > [ InternalId = 854698491929 , Hostname = EXSERVER . exchange2016demo . com ] Queued post for delivery |
Then at that place'south no specific configuration required on the server or the connectors to let this scenario, however information technology is recommended that you use a DNS alias instead of the real server name. This volition allow you to configure all of your devices and applications with the DNS alias, and you tin later movement that DNS alias to point to a dissimilar Substitution server during a migration.
External SMTP Relay with Exchange Server 2016
Continuing from the previous demonstration, let's see what happens if I attempt to utilise Telnet to send an e-mail message from a valid internal accost to an external recipient.
| 220 EXSERVER . exchange2016demo . com Microsoft ESMTP MAIL Service ready at Thu , 22 Oct 2015 12 : 04 : 45 + thousand helo 250 EXSERVER . exchange2016demo . com How-do-you-do [ 192.168.0.30 ] postal service from : adam . wally @ exchange2016demo . com 250 2.one.0 Sender OK rcpt to : exchangeserverpro @ gmail . com 550 5.seven.54 SMTP ; Unable to relay recipient in not - accepted domain |
An SMTP error code "550 5.seven.54, Unable to relay recipient in not-accepted domain" is received instead. The receive connector volition not permit an anonymous, unauthenticated sender to relay to external domain names, which prevents your server from being exploited as an open relay.
There are 2 ways you lot tin resolve this and permit your devices and applications to transport to external recipients:
- Using authentication for SMTP connections
- Configuring an anonymous SMTP relay connector
External SMTP Relay with Exchange Server 2016 Using Authentication
The start method is to employ authenticated SMTP connections. Exchange Server 2016 has a receive connector designed to be used by clients that need to send via SMTP called "SERVERNAMEClient Frontend SERVERNAME", for example "EXSERVERClient Frontend EXSERVER" in my test environment.
| [ PS ] C : \ > Go - ReceiveConnector Identity Bindings Enabled -- -- -- -- -- -- -- -- -- -- -- - EXSERVER \ Default EXSERVER { 0.0.0.0 : 2525 , [ :: ] : 2525 } True EXSERVER \ Client Proxy EXSERVER { [ :: ] : 465 , 0.0.0.0 : 465 } Truthful EXSERVER \ Default Frontend EXSERVER { [ :: ] : 25 , 0.0.0.0 : 25 } Truthful EXSERVER \ Outbound Proxy Frontend EXS . . . { [ :: ] : 717 , 0.0.0.0 : 717 } True EXSERVER \ Client Frontend EXSERVER { [ :: ] : 587 , 0.0.0.0 : 587 } True |
Minimal configuration is required to get this working. Assuming you've already configured an SSL document for Commutation Server 2016, and added a DNS alias for your SMTP devices and applications to use (I'm using a DNS alias ofmail.exchange2016demo.com in this instance), you should then also set the TlsCertificateName for the receive connector.
Use Go-ExchangeCertificate to identify the thumbprint of the SSL certificate you'll be using.
| [ PS ] C : \ > Get - ExchangeCertificate Thumbprint Services Subject -- -- -- -- -- -- -- -- -- -- -- -- - FC5259C0528657EF22BB818CA9B23FD220A9DE83 . . . WS . . CN = mail . exchange2016demo . com , OU = IT , O = LockLAN Systems Pty Ltd , . . . FE6528BE1548D81C794AE9A00D144FF3D16E0CD2 . . . . Due south . . CN = Microsoft Exchange Server Auth Certificate DAB089E53CA660DEF7B8EE303212C31C0E3D3499 IP . WS . . CN = EXSERVER 17839AF62AA3A1CBBD5F7EC81E92A609976D8AD9 . . . . . . . CN = WMSvc - EXSERVER |
The syntax of the TlsCertificateName string is made upward of two dissimilar attributes of the certificate, so I employ the post-obit commands to apply the configuration to my receive connector.
| [ PS ] C : \ > $ cert = Get - ExchangeCertificate - Thumbprint FC5259C0528657EF22BB818CA9B23FD220A9DE83 [ PS ] C : \ > $ tlscertificatename = "<i>$($cert.Issuer)<s>$($cert.Subject)" [ PS ] C : \ > Set up - ReceiveConnector "EXSERVER\Client Frontend EXSERVER" - Fqdn postal service . exchange2016demo . com - TlsCertificateName $ tlscertificatename |
To test using the Client Frontend connector to send an email bulletin I'm going to utilise PowerShell's Send-MailMessage cmdlet instead of Telnet. Kickoff, capture some valid credentials to use for authentication.
| PS C : \ > $ credential = Get - Credential |
Next, use the Send-MailMessage cmdlet with parameters specifying the server, to and from addresses, subject line, and the port number.
| PS C : \ > Transport - MailMessage - SmtpServer mail service . exchange2016demo . com - Credential $ credential - From 'adam.wally@exchange2016demo.com' - To 'exchangeserverpro@gmail.com' - Subject area 'Test electronic mail' - Port 587 - UseSsl |
In the above example the email is successfully received by the external recipient. So any device or awarding on the network that tin use authenticated SMTP can exist set up to utilize that connector listening on port 587 on your Exchange 2016 server.
External SMTP Relay with Substitution Server 2016 Using Bearding Connections
When authenticated SMTP is not an option you can create a new receive connector on the Exchange 2016 server that will permit anonymous SMTP relay from a specific list of IP addresses or IP ranges.
In the Exchange Admin Middle navigate to mail flow and then receive connectors. Select the server that yous want to create the new receive connector on, and click the "+" button to offset the sorcerer.
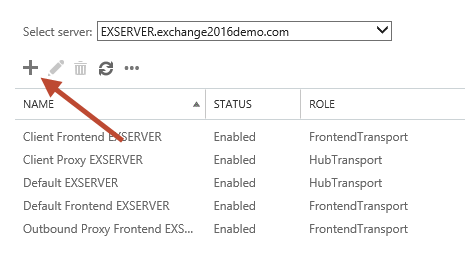
Give the new connector a proper name. I similar to keep the name consistent with the other default connectors. Set up the Role to "Frontend Ship", and the Type to "Custom".
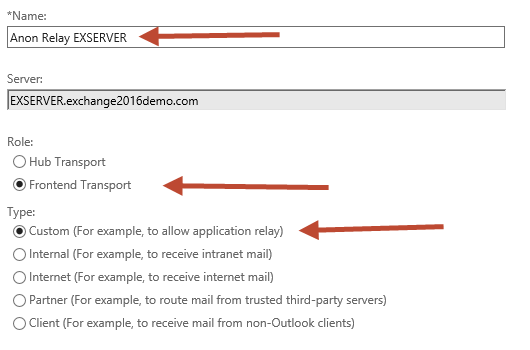
The default Network adapter bindings are fine. This represents the IP and port that the server volition be listening on for connections. Multiple receive connectors on the Frontend Send service can heed on the same port of TCP 25.
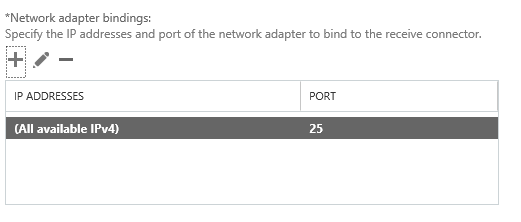
Remove the default IP range from the Remote network settings, and then add in the specific IP addresses or IP ranges that yous desire to allow anonymous SMTP relay from. I do non recommend calculation entire IP subnets that contain other Exchange servers as this can crusade issues with server to server communications.
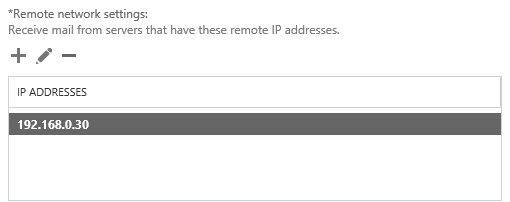
Click End to complete the wizard, then in that location is some boosted configuration still required.
In the Exchange Management Shell run the following two commands.
| [ PS ] C : \ > Set - ReceiveConnector "EXSERVER\Anon Relay EXSERVER" - PermissionGroups AnonymousUsers [ PS ] C : \ > Get - ReceiveConnector "EXSERVER\Anon Relay EXSERVER" | Add together - ADPermission - User 'NT Dominance\Anonymous Logon' - ExtendedRights MS - Exch - SMTP - Take - Any - Recipient |
We tin now test the connector using Telnet from the IP address that was added to the remote network settings of the receive connector. In my test environs that IP address will now be allowed to send email from any email address (whether it is a valid internal address or not) to whatever external address.
| 220 EXSERVER . exchange2016demo . com Microsoft ESMTP Post Service ready at Thu , 22 Oct 2015 12 : 59 : 39 + 1000 helo 250 EXSERVER . exchange2016demo . com Hi [ 192.168.0.30 ] postal service from : test @ test . com 250 2.ane.0 Sender OK rcpt to : exchangeserverpro @ gmail . com 250 2.1.5 Recipient OK Data 354 Showtime mail input ; end with . Subject : test . 250 2.6.0 < e1739c5f - db11 - 4fdd - aa27 - a9702bc15b15 @ EXSERVER . exchange2016demo . com > [ InternalId = 863288426497 , Hostname = EXSERVER . exchange2016demo . com ] Queued mail for delivery |
Additional Considerations
Hither's some boosted items that you should consider when you lot're providing SMTP relay services with Substitution Server 2016 for your environment.
High Availability and Load Balancing
If you desire to provide a highly available SMTP service then a load balancer is the natural solution. If you program to load remainder you lot'll need to ensure that the same receive connectors exist on all of the servers in the load balanced pool. This means creating the aforementioned relay connector on multiple servers and managing the same list of permitted IP addresses on those connectors.
Yet, as y'all'll see by reading my commodity on bug with load balancing SMTP traffic, when a load balancer is source NATing the connections the but IP address that will appear to the Exchange server is that of the load balancer itself, non the source device or application. While this simplifies the receive connector configuration (only the load balancer IP needs to exist added as an allowed IP) it opens up a number of concerns:
- Admission control (which IP'southward are allowed to send) needs to be applied at the load balancer, or yous chance having a wide open anonymous SMTP relay service on your network
- Depending on the load balancer, health probes to the Exchange servers may not detect all wellness conditions, resulting in traffic beingness sent to unhealthy servers (and failing)
- Connections made via the load balancer are anonymous and in some cases untraceable to the source IP (depending on what logging your load balancer is capable of)
You tin read more than almost these bug here.
If a load balancer is non an option for you and you all the same want some high availability for SMTP services, then y'all can consider DNS round robin. However, many devices and applications practise not handle DNS round robin equally well as Outlook or a spider web browser would. Some devices, when they endeavour a connectedness to one of several IP addresses available in DNS round robin and that IP address is not responding, will not try other IP addresses that are bachelor and will simply consider the connexion attempt failed. And then it really depends on how well your devices and applications deal with that state of affairs as to whether DNS round robin will exist suitable for your environment.
Security vs Convenience
A lot of organizations simply go with the bearding relay choice and set upward a connector that allows wide ranges of IP addresses to relay email anywhere. This is the simplest arroyo, simply conspicuously not the all-time in terms of security and auditing. Bearding relay relies on trusted, identifiable IP addresses. If the IP addresses are in a DHCP pool, are associated with a load balancer (see above), are multi-user (such as terminal servers), or the IP/host itself is compromised in some way, and then your ability to trace emails back to the existent source is difficult if not impossible.
Although authentication adds some complexity, it may be worth it from security perspective. However it does mean managing credentials for all of your devices and applications. Sharing SMTP credentials across multiple systems might seem like a style to avoid complexity, but information technology re-introduces the issues associated with anonymous SMTP.
Encryption
In the tutorial higher up I demonstrated configuring a TLS certificate proper name for a receive connector and also used TLS/SSL for my testing with Ship-MailMessage. If y'all are going to apply hallmark for SMTP in your surround, or the SMTP traffic is in whatsoever style sensitive, then you should protect it with TLS/SSL encryption.
Multiple Receive Connectors
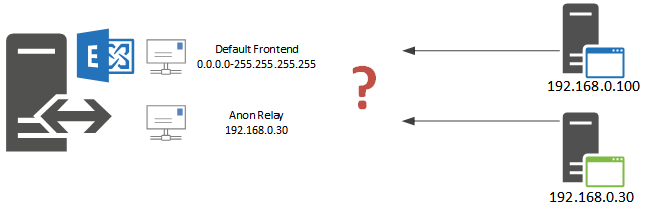
You lot may be wondering how the Exchange server is able to differentiate between traffic destined for one receive connector vs another receive connector, when both of them are listening on the same IP address and port number, for instance "EXSERVERDefault Frontend EXSERVER" and "EXSERVERAnon Relay EXSERVER".
The answer is in the Remote network settings of the receive connectors. Exchange will utilize the receive connector that is the about specific match for the source IP address of the SMTP connection.
In my examples above this means that the default connector with its remote network settings of 0.0.0.0-255.255.255.255 (which is basically "anywhere") is less specific than the relay connector with its remote network settings of 192.168.0.30. So when an SMTP connexion comes from IP 192.168.0.30 to port 25 on the server it will be handled by the relay connector, while everything else connecting to port 25 will be handled past the default connector.
Troubleshooting
I of the most common issues when troubleshooting receive connector behaviour on an Substitution server is determine which connector is actually handling a given connection. At that place are two ways to arroyo this blazon of troubleshooting.
The first is to set different SMTP banners on each connector. Commutation MVP Jeff Guillet has a PowerShell example that y'all can run to configure each connector's SMTP banner with the name of the connector itself, so that when you connect with Telnet you can immediately see which receive connector you've connected to.
| [ PS ] C : \ > $ rc = Become - ReceiveConnector - Server EXSERVER [ PS ] C : \ > $ rc | % { Set - ReceiveConnector $ _ . Identity - ProtocolLoggingLevel Verbose - Banner "220 $_" } |
Now when you lot use Telnet to connect you lot volition run across the connector proper noun in the imprint.
| C : \ > telnet exserver 25 220 EXSERVER \ Anon Relay EXSERVER |
The other troubleshooting method is to employ protocol logging. In the PowerShell example above the protocol log level for each connector was also set to "Verbose". You tin set this on private connectors if yous need to by running Fix-ReceiveConnector.
| [ PS ] C : \ > Set - ReceiveConnector "EXSERVER\Anon Relay EXSERVER" - ProtocolLoggingLevel Verbose |
You can then review the protocol logs to make up one's mind what is happening to SMTP connections. I generally recommend you leave protocol logging enabled for receive connectors at all times.
Summary
This article demonstrates how Commutation Server 2016 can be used to provide SMTP relay services to devices and applications on your network. Every bit yous can see there are multiple approaches that you can take to accomplish this, each being suitable for different scenarios, and each having some pros and cons associated with it.
Internal relay needs are already met with the default configuration of an Substitution 2016, and authenticated SMTP for external relay is as well available with minimal setup. When anonymous relay is required an additional receive connector can exist easily configured.
I do recommend that you consider your actual requirements and implement the most advisable solution to see them, instead of merely configuring an anonymous relay connector for all devices and applications on your network.
reyesmamrainy1941.blogspot.com
Source: https://practical365.com/exchange-2016-smtp-relay-connector/
Post a Comment for "Too Many Concurrent Mail Connections Try Again Ms Outlook"